Project Poster Content
Title and Author: "Steganography Using Computer Images", William Barratt
Abstract: An investigation into methods of steganography using computer images, covering various steganography algorithms and image file types.
Background: The definition of "steganography" is "hiding a secret message within a larger one in such a way that others can not discern the presence or contents of the hidden message." Steganography has existed since ancient times and has progressed to modern forms of hiding data, including microdot images, and more recently, computer steganography. For example, some have theorized that Al-Qaeda terrorists have used computer image steganography to communicate secretly. [definition source: The Free On-line Dictionary of Computing, © 1993-2001 Denis Howe, accessed through dictionary.com]
Development:
Choosing a File Type: Many standards exist for computer image files; common Internet image file types are GIF, JPEG, and PNG. When choosing a file type to write a steganography program, several important characteristics must be considered. The first consideration is whether the file type will be "lossy," meaning it loses data in conversion and thus cannot reliably preserve a hidden message. JPEG is notorious for being lossy, and makes a poorer choice than lossless formats like PNG. The second consideration is how noticeable a small change to the file will be. Image files that use a larger color palette are less susceptible because of the tiny difference between two adjacent shades of color.
This project first used the PGM image file standard, because the simplicity of its files make it easy to read and manipulate. Its small palette of 256 shades of gray is large enough that a change to the low-order bit is imperceptible, and its uncompressed array of pixel values is easily viewed in a text editor to check the program's output for correctness.
Choosing an Algorithm: There are a multitude of schemes for computer image steganography, and it is important to choose an algorithm that creates no change noticeable by casual comparison, i.e., the changes are detectable only by a byte-to-byte comparison. The algorithm can also include encryption, but given that the strategy of steganography is hiding a message in one image within a sea of images, encryption is not compulsory.
A very simple algorithm involves modifying the low-order bits of pixel values so that the low-order bits of the pixels form a sequence of ASCII characters. The pixels do not change noticeably in color, and the file size remains the same. The biggest issue with this algorithm is that the message that can be hidden is limited severely by the number of pixels. Other algorithms may change more of the pixel value to gain more space.
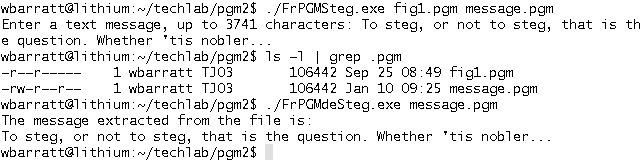
Basic Problem: Create a program that, given an existing image file, hides a text message within the image file without changing the file's size or appearance to the human eye. The message must be readable by a program given the modified image but not the original image file.
Appropriate images: (1) screenshot of terminal during program run, (2) image "before and after" program run
Original image, fig1.pgm (converted to JPEG)

Image with message included, message.pgm (converted to JPEG)

Screenshot of terminal during program run